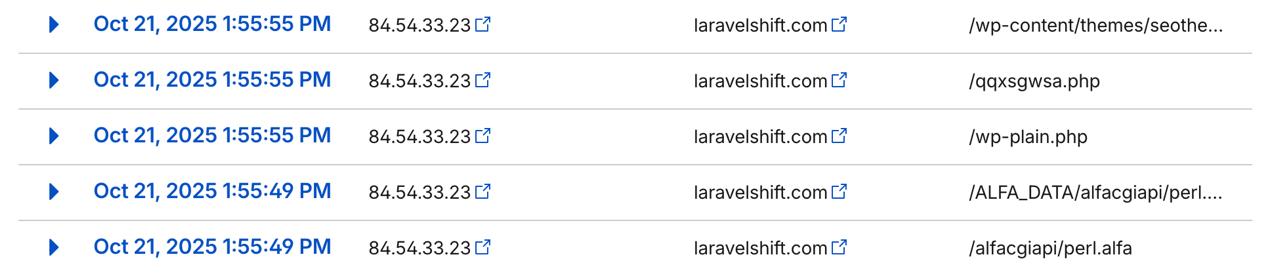
Your Laravel application is bombarded with invalid requests. They're made from all sorts of bots. Most probe for attack vectors. Common website endpoints to exploit. Things like /wp-admin/, login.php, or .env.
For the most part, your web server simply returns a 404 Not Found. But it still processes the request. Depending on how popular your site is, you may receive dozens or even hundreds of these requests a second.
Over the last month, I've been on a quest to improve the load times for laravelshift.com. By the 80/20 Rule, a majority of the load time is responding to a request. Sure things like database queries or complex calculations take time. But it's nothing compared to the overall time it takes to connect, process, and respond to a web request.
So, my goal has been to reduce the requests to my web server. I'll cover more strategies in future articles. In this article, I'll reduce the number of requests by preventing invalid ones. This frees up my web server to process valid requests. Less traffic to my web server also matters if I use per request services - like Nightwatch.
That's actually where this idea came from. Michael Dyrynda wrote a post about protecting Laravel Cloud endpoints. He noticed invalid requests in his logs. These were burning through his request quota.
He set up a security rule within Cloudflare to block requests to these endpoints. This got me thinking, "What if could block all invalid requests?". I remember a lesson from my CS Security course - it's better to specify what you allow, than to specify what you don't allow. What you allow is a known, finite list. What you don't allow is an unknown, infinite list.
We know what endpoints are allowed without our Laravel application. We can list them by running artisan route:list. Turning this into a valid rule is pretty straightforward. Anything that has a parameter, such as a model binding, may be turned into a wildcard expression. Everything else is an exact match.
For example, the following routes:
Route::get('/', [HomeController::class, 'index'])->name('home');Route::view('/faq', 'faq');Route::get('shifts', [ShiftController::class, 'index'])->name('shifts');Route::get('workbench/{task:slug}', [TaskController::class, 'show'])->name('task.show');Could be represented by the following expression:
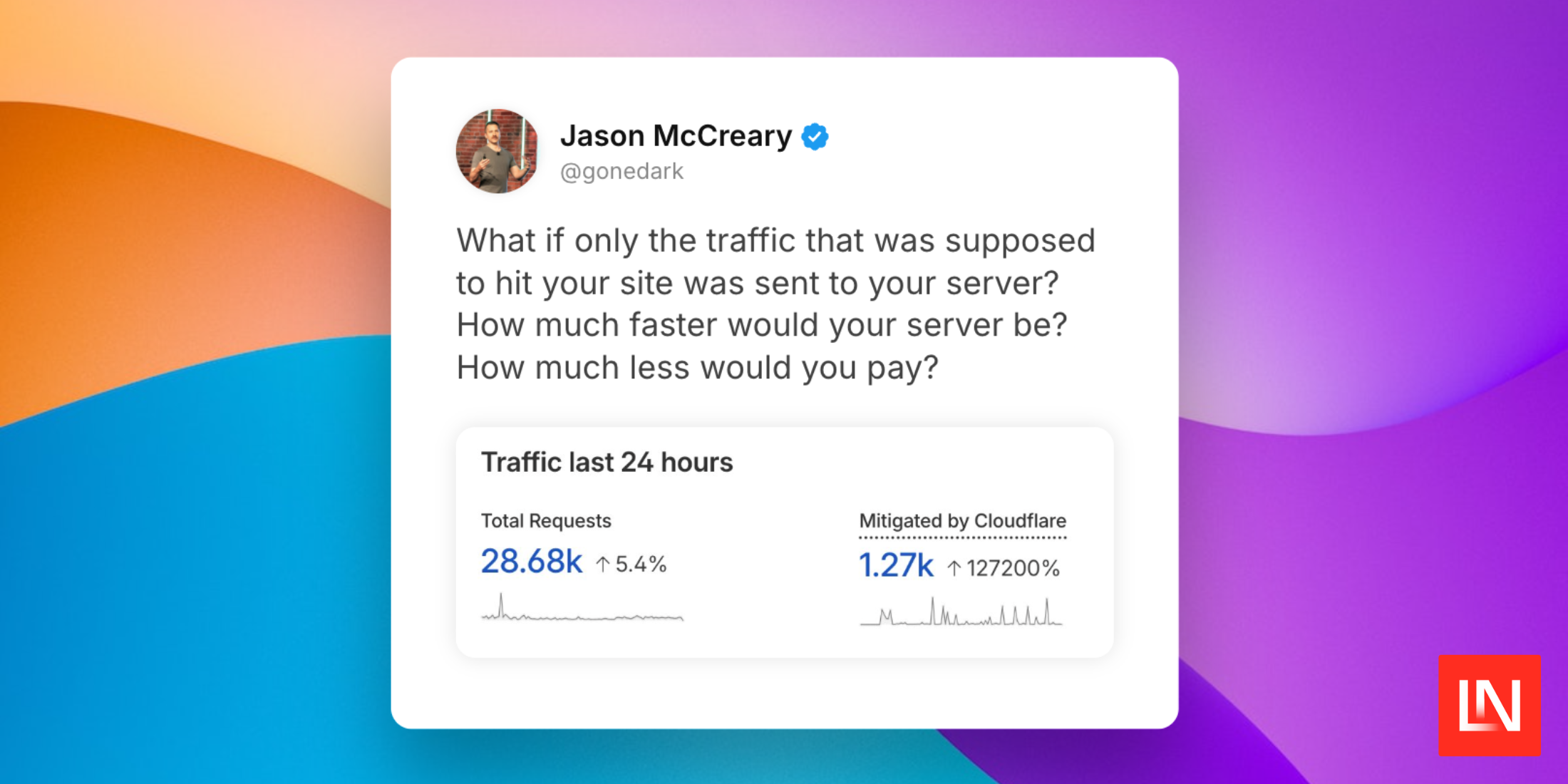
not (http.request.uri.path in {"/" "/faq" "/shifts"} or http.request.uri.path wildcard "/workbench/*")I enabled such a security rule in Cloudflare for laravelshift.com. Now my application only allows traffic to existing endpoints. Anything else will be blocked by Cloudflare. In just one week, over 5000 invalid requests were blocked. Freeing up my web server to process valid requests.
 As always, this comes with a tradeoff. The Cloudflare free plan only allows the action to Block. This renders a Cloudflare error page with a
As always, this comes with a tradeoff. The Cloudflare free plan only allows the action to Block. This renders a Cloudflare error page with a 403 Forbidden response. Ideally you might respond with a simple 404 Not Found. I'm comfortable with this given the traffic I'm blocking. But legitimate users with a typo or broken link will receive this Cloudflare error page. This is mitigated by ensure you have redirects for common typos or renamed paths.
If you're interested in creating one of these rules, JT Smith is working on a package which provides a command to generate the rule for your application. It will also optimize the rule, and condense it under Cloudflare's 4096 character limit.
If you're interested in making your Laravel apps respond crazy fast, check out my Fast Laravel video course.